A Secure Foundation Is Critical
Written by Jeff Watts
The foundation of my house
Many years ago, my daughter came home to visit and got my wife and me hooked on home improvement shows like Fixer-Upper. We love watching the home makeover projects and brainstorming ideas for our new "forever" home in the country. To make it even better, the builder for my new home is one of my best friends. He's passionate about creating a well-engineered, well-designed house with a strong foundation. Every now and then, he'd let me "help" – and let me tell you, I gained a whole new appreciation for everything that goes into building a solid home from the ground up.
This experience gave me a great analogy for cybersecurity. The design and architecture of your systems and networks are just like the foundation of your house. If the foundation is solid, everything else will fall into place – Chip and Joanna can come in, remove a few walls, get rid of the popcorn ceiling, install some shiplap, and make it all look amazing. But if the foundation is shaky, that's when the real trouble starts – Chip has to have a pretty uncomfortable conversation with the homeowner about how much more it will cost to fix it.
Hands-On Experience Building a House
In the same way, a secure foundation in cybersecurity enables you to make changes, updates, and improvements – safely and securely. It shouldn't be a barrier to productivity. If cybersecurity is slowing you down, then your approach isn't working. It starts with your systems' foundation – it should be built securely from the ground up, not just "bolted on" later. With a solid foundation, you can better support your mission and ensure your data's confidentiality, integrity, and availability.
This is why RPI Group renamed our Cybersecurity department to Cyber Solutions and changed my title to Lead Solutions Architect. We realized that cybersecurity isn't just about hardware and software but includes policies, procedures, configuration, patch management, and even company culture. All these pieces play a role in keeping your foundation strong and secure.
Nowhere is this more critical than in Critical Infrastructure. At RPI Group, we build systems and networks supporting Critical Infrastructure from the ground up with secure, scalable, and well-documented architecture. We ensure our foundation is solid by verifying compliance with DISA STIGs, industry best practices, and guidance from NIST, NSA, DHS, and partners like Dragos. This approach gives our customers a secure architecture, allowing them to scale and make changes safely.
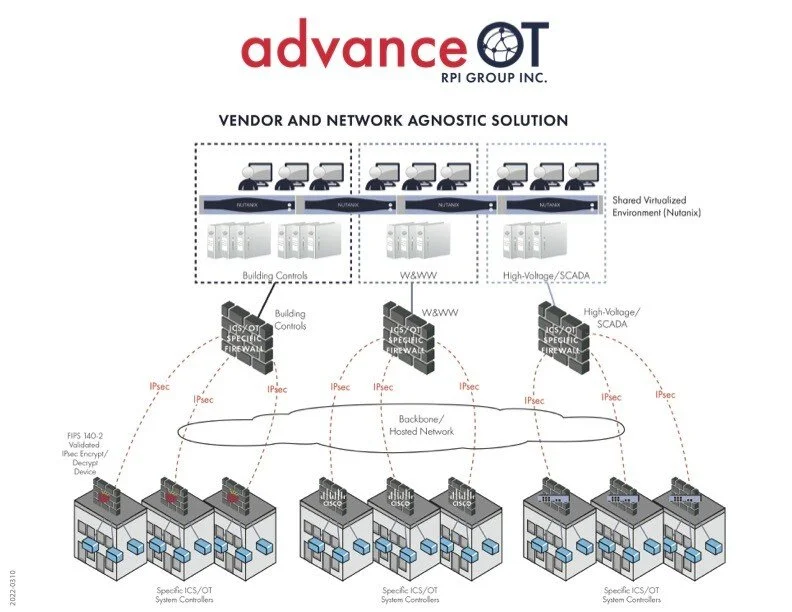
advanceOT
Take, for example, our new 5G solution, advance5G. It's built on COTS hardware, an Open-Source operating system with a FIPS 140 validated kernel, Open-Source 5G Core (OAI and Open5GS), and an Open Radio Access Network (ORAN). We apply all relevant DISA STIGs and NIST RMF controls – all documented and validated. It's just one way RPI Group ensures that cybersecurity becomes an enabler, not a roadblock, for our customers.
Do you need help designing and building a secure foundation (architecture)? At RPI Group, we're here to provide solutions and training to keep your systems secure and your operations resilient. Let's discuss how we can work together to protect your critical assets.
#CyberSecurity #CriticalInfrastructure #CyberDefense #SmallBusiness #5G #RPIGroup #InfrastructureProtection #SystemArchitecture